Strengthening Security with SAP Cloud Identity and Access Management
As businesses move to the cloud, securing access to critical applications and data is more important than ever. Unauthorized access, data breaches, and compliance violations are constant threats, making Identity and Access Management (IAM) a fundamental aspect of cybersecurity. SAP Cloud Identity and Access Management (IAM) provides the tools enterprises need to authenticate users, manage access, and enforce security policies efficiently.
This article explores SAP’s Cloud IAM solutions, detailing their key components, best practices for implementation, and strategies for overcoming common challenges. By the end, you’ll have a clear understanding of how to leverage SAP IAM to protect your organization.
Understanding SAP Cloud IAM Services
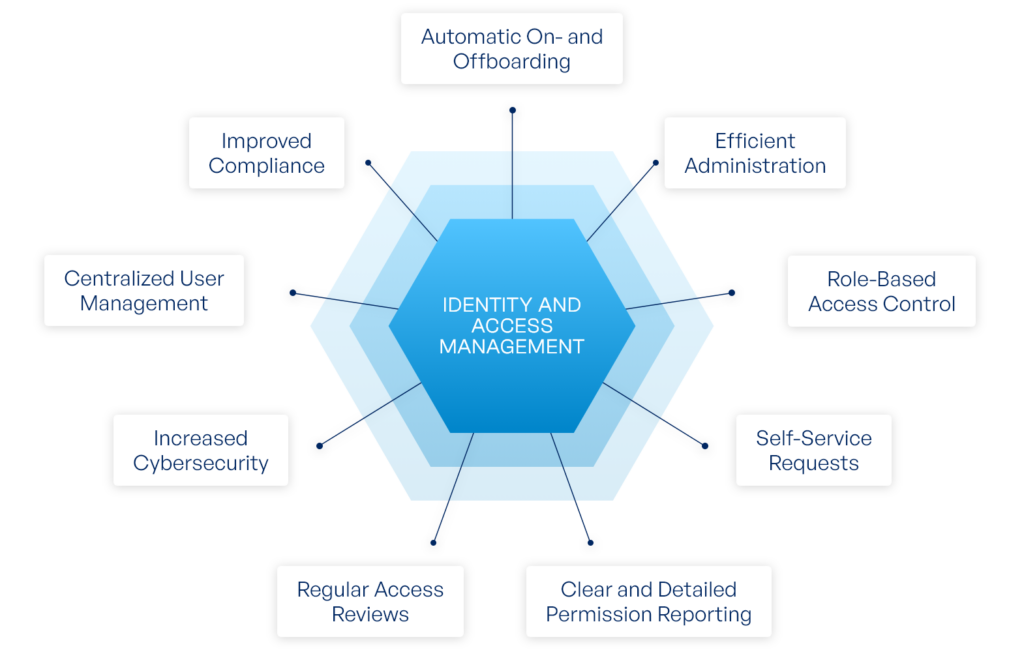
Identity Authentication Service (IAS)
The Identity Authentication Service (IAS) acts as a security gateway, ensuring that only authorized users can access SAP and third-party applications. It simplifies authentication processes while maintaining high security standards.
Key Features:
- Single Sign-On (SSO): Users log in once and gain access to multiple applications without needing to re-enter credentials.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring additional verification beyond passwords.
- Risk-Based Authentication: Evaluates login attempts based on user behavior, device, and location to detect suspicious activity.
- Federated Authentication: Integrates with existing corporate identity providers like Microsoft Active Directory, simplifying access management.
Identity Provisioning Service (IPS)
The Identity Provisioning Service (IPS) automates user lifecycle management, ensuring that employees, partners, and contractors have appropriate access based on their roles.
Key Features:
- Automated Provisioning: New users are granted access based on predefined rules, reducing manual workload.
- Deprovisioning: Access is automatically revoked when employees leave or change roles, minimizing security risks.
- Cross-System Integration: Syncs identity data across cloud and on-premise applications for consistent access control.
- Role-Based Access Control (RBAC): Ensures users only receive permissions relevant to their job functions.
Best Practices for Implementing SAP Cloud IAM
Define a Clear IAM Strategy
Before deploying SAP IAM, outline your organization’s identity management policies. Determine access levels for different user roles and document security requirements.
Strengthen Authentication Mechanisms
Use MFA to prevent unauthorized access, enforce password policies, and implement risk-based authentication to identify and mitigate potential threats.
Automate User Lifecycle Management
By leveraging IPS, businesses can automate the onboarding and offboarding process, ensuring security policies are consistently enforced.
Monitor and Audit Access Activities
Regularly review IAM logs and integrate them with a Security Information and Event Management (SIEM) system to detect anomalies and security incidents.
Ensure Compliance with Regulations
Adopt IAM policies that align with regulatory requirements such as GDPR and SOC 2. Regular audits help verify compliance and identify gaps.
Overcoming Common Challenges
Integration with Legacy Systems
Many organizations struggle to integrate IAM with older systems. Using APIs, middleware, and custom connectors can bridge this gap.
User Adoption and Training
Ensuring employees understand IAM policies is critical. Conduct training sessions to help users follow security best practices.
Managing Privileged Accounts
Restrict administrative access and apply the principle of least privilege (PoLP) to minimize risks associated with privileged accounts.
Securing the Future with SAP Cloud IAM
Identity and access management is no longer just an IT responsibility—it’s a business necessity. SAP Cloud IAM provides the security, automation, and scalability organizations need to protect critical assets while ensuring seamless access for users. By implementing strong authentication, automated provisioning, and continuous monitoring, businesses can reduce security risks and improve operational efficiency.
As cyber threats evolve, so must identity management strategies. A proactive approach to IAM not only strengthens security but also enhances compliance, user experience, and overall business resilience. Investing in a comprehensive IAM framework today ensures a safer, more agile enterprise for the future.







